“Have I been #hacked?” Odds are, yes. Find out why—and what you can do about it—by reading these email address security tips.
Has Your Account Been Breached? Email Address Security Tips
- Our topic today is one of those unfortunate necessities. I wish we could be talking about something fun like productivity apps or content creation. But I think it's my responsibility from time to time to make sure that you are aware of a lot of the security issues that we face online. And today I wanna talk about the danger of having our accounts compromised, our email addresses and passwords compromised, not by something necessarily that we've done, but rather by an external breach to a service that we are subscribed to. This happens on an alarmingly frequent basis. Just looking at the news, you will see lots of stories just like this one. The CPA discloses a security breach, 329,000 people. 329,000 and look what it includes. Names, home addresses, email addresses, this is not unusual, in this case 329,000 people, not even that huge a breach. For example, these guys at EasyJet, oh my goodness, 9 million customers affected by a security breach. And if we take a look, what do they have? Including email addresses and travel details. Well, that's special, isn't it? This is the sort of thing that we face, not through any fault of our own, but where the security of an account that we have signed up for, a service that we use, when they get attacked by hackers and the information gets stolen from then, our security is then at risk. So this is what I want to address today on Dotto Tech. Steve Dotto here, how the heck you doing this fine day? I know, I know, I know, I'd be doing a lot better, Steve, if you were talking about something fun and you weren't being the heavy and talking to us about security. Well suck it up, buttercup, this is for all of our good. Our privacy and security is under attack, is under siege all of the time. At 24 hours a day, seven days a week, people are trying to break into websites, websites and services that we, our customers have and what are they trying to break into get? They're trying to break in to get access to our information, our email addresses, our credit card numbers, our passwords, our address, any information they can get about us is worth money to them. Now there's basically two different types of attacks that are happening on an ongoing basis. I'm sure there's more but there's two that I'm gonna talk about today. The first are the phishing attacks, they're internal attacks where people come after us individually and try and steal our information directly from us. And you've all received emails like this. Netflix says, oh my gosh, I have to update my payment details or I'm not gonna be able to watch the next season of whatever it is I want to watch. I better click on that button right now and update my payment information to make sure everything's okay. Of course, this is what's called a phishing attack. This isn't from Netflix but it's from somebody who's trying to steal our information. And were I to click on this email, I would probably then end up giving the whoever that is access to my Netflix account, and who knows what other information they could glean at that particular time. These phishing attacks happen all the time in email. Increasingly, we're starting to get them now in text messaging, you recognize them and education is our best defense against this sort of an attack. The other type of attack is an external attack. And that's really what I want to talk about today. And external attacks aren't focused on us, but instead they're focused on services that we use, websites that we have accounts with or services that we have accounts with. They are constantly under siege and occasionally they get breached, and when they get breached, a variety of different types of information can be stolen. Now it can be really as benign as they have access to nothing because they get a bunch of encrypted email addresses that they can't even see what the email address is. And we aren't the worst for where. Or they can also end up with plain text information, our email address, perhaps passwords, perhaps credit card numbers or address or some other personal information, something that they can use against us in order to leverage that information into other accounts and proceed down a road which is not a destination that you or I want to go. 24 hours a day, seven days a week, virtually all websites are under attack. They use robots, they use bots to try and find security breaches, and try and get in to all different online services. And when they find a weakness, they focus on it and then they try and steal the information. If you have a few moments, just head over to Wikipedia and take a look at a list of data breaches. This is literally just the tip of the iceberg here. Lemme change the sorting criteria. And let's do it by the most current data breach. The earliest one they have is back in, what was it? 2004 is the first one they list here, the AOL breach, remember that 92 million? good times. But let's look at the more frequent, more recent ones. Here we see 56 million accounts compromised this year. Another one, Marriott, 5.2 million. You probably heard about that one in the press. Adobe 2019, 7.5 million. Sadly, Adobe has been hacked several times. Canva, 140 million accounts. Capital One, 106 million accounts, the numbers just add up. And these are the big ones. There are thousands and thousands of smaller sites that are compromised, most of which we will never hear about often even if you are an account holder with that particular service. So what's in it for the hacker? What is their motive in behind all of this? Well, obviously, it's profit, and they make money a variety of different ways. I'm no expert, but I know that in some cases, the hackers will reach out to the victim, reach out to the site that they've breached and they will try and extort some funds from them. That's one way that they can profit from their venture. Or they can just take the information and they can sell it on the dark web, there's a variety of different ways that they can profit from their malfeasance. But here is the thing that is really a concern, at least I consider it to be a major concern, is the amount of time that it takes for us to identify that a breach has occurred. It takes an average of 209 days, let me say that again, 209 days from the time a breach occurs till the time we're informed about it in the public. Now the company might know a little bit earlier than that, but that's how much time it take s for us to find out. And believe it or not, for them to close a breach, it takes them over 300 days. I think it's 314 days on average, from a time a breach is started till that breach is closed. It's like looking into outer space at a distance star, the light you see happened years and years and eons ago. That's the kind of timeframe that we're talking about. The breaches that we know about today happened last year, it's frightening. So what can we do about it? Well, we can do a few things. There's some proactive things we can do and we can make sure that we are informed when our email address and our accounts have been compromised. Now before I jump into showing you that, I wanna tell you that today's video is sponsored by the Breach Report, which is one of the services which I'm going to be talking about today. If you go to the end of the video today or you stick around to the end, I'll take you through the entire Breach Report story. But let's talk first about the first thing that we wanna do which is become informed. Now it should probably go without saying that if it takes 209 days for the public to become aware of a breach, that's a lot of time for a lot of damage to be done before we're aware that are our address has even been compromised, or our accounts have even been compromised. So that's where the Breach Report steps in. The Breach Report is constantly monitoring the web and the dark web to find information about breaches and then returning to us if they discover our information has been included in one of the breaches or one of the leaks. You can just do it for yourself, this is actually a really fascinating process, just go to the Breach Report, and enter your email address or your domain name, and when you enter your email address, they will do a quick scan of the web, and they will return and let you know how often your email address has been compromised. And this is my personal email address. And it has been breached six times, oh my gosh. And now you might be horrified by the number you see or you might just be really happy with the number you see here, but this is the number of times that they found my email address in existing breaches that I knew nothing about. Now the process is you sign up for an account, which is free, and they will send you a report. And the report looks like this. The report takes you through each of the breaches that your email address has been discovered in. And as I look through, I can see way back in 2012, I've had this email address for a very long time, it was found in a LinkedIn breach and in a Myspace breach in 2016, in Patreon, oh my gosh, Patreon. Yeah, remember that now, Patreon was breached in 2015. This is a combination, there was a big leak of a whole bunch of different smaller websites that was all combined together. My email address was found in there. It was found in a Bitly breach in 2014. And in, oh, Dubsmash. I'm not particularly proud of that one. But those are the places that my email has been compromised. And so this is just the beginning of us informing ourselves about where the risk occurs. And obviously, with each one of these, I have to think back what was I doing about password protection at the time, and in recognizing that at that point there, my information was out there and available for anybody who wanted access to it. It's a little bit of a scary and a little bit of an eye-opening thing. I wanna show you a few of the other features that they have here. This is one which I find really valuable to browse through before we go into detail about the breaches that my email address has been included in. And this is their catalog. This is ever so valuable. Breach Report is constantly monitoring the dark web and they're bringing back reports of all of the different breaches that have occurred. Now here we see a catalog of the most recent breaches and every day, new breaches appear here in the catalog. And this is the thing that is where we're really kind of comes home. So many of these accounts are small accounts. 2,100 hacked accounts, 2,200 hacked accounts, look this, a small one, 2,000 hacked accounts. So it's not just the hundreds of thousands in the millions, but all of these small sites are constantly under pressure as well. And often when they get hacked, owners of that site have very little sophistication as far as understanding the security settings. And they might not even know how to inform all of their users that they've been hacked. So we can't rely on them to inform us in a timely matter, that our, if we happen to have an account with one of these, that our account has been compromised, whereas Breach Report will return that information to us as they discover it. Now what do they bring back? This is where it gets really interesting. And I have to admit, this is the part of the entire process that shook me up the most. When I go in and I take a look at my email address here and I go into the detail screen that they offer, it tells me each of the breaches again in a digest here, but then underneath here are all of the passwords or any other information that was gleaned at the same time. And if I take a look here, you have to re affirm your account at this point here, they go through and they actually tell me here, the passwords that were attached to the accounts at the time of the breach. Now hackers don't always manage to marry a password to an email address. But when they do, it can be devastating 'cause so many people have poor password management, and so that the same password and username combination is used in multiple accounts, and at that point there, the hacker can get into a variety of different accounts from you and they can start to slowly take over and cause some real damage. But look here, out of the six times that my email address has been compromised, I recognize one, two, three of those passwords as passwords that I used regularly in the past for my temporary accounts, and this sends a shiver up my spine. So informing ourselves of when breaches and how breaches have occurred is one thing that we can do to protect ourselves. But what can we do that's a little bit more proactive about protecting ourselves? And you know what I'm going to tell you here at this particular point. First and foremost is to have a good password strategy in place. And that involves for most of us within using a password manager. Now we like to use LastPass here, but I don't care what password manager you choose to use, they will all offer you a far greater degree of security than any manual system that you can come up with. And make sure that you change your passwords on a regular basis. The frequency of these hacks should be an impetus for you to change your passwords on an ongoing basis, and good password managers help you with that, they help you to... I'm doing something right now. Yeah, go over the bed, you can sit there. Where was I? Good password managers will help you in the process. They will help you... They will facilitate you changing your password, and they will even remind you on a regular basis that you need to change your password. So that's number one, good password management. And the second thing and I don't know why more people don't do this, but please, please use two-factor authentication, we have a video on it, it's easy to do, most major websites now support it, but two-factor authentication, even if your email address and a password gets compromised somewhere, it is going to be an insurance policy that should help you protect your account and your information. So two-factor authentication is as far as I'm concerned, a must use in this day and age. The third thing that I'm gonna recommend, I'm not sure many other security experts would necessarily recommend this but it's a really practical solution and that is using a decoy email address for sites that you are not 100% committed to. Here, we all go through this experience, we go and we visit a site, we visit a service and we wanna take it for a test run, we're not sure we wanna buy it, we're not sure we wanna use it. So rather than use my real email address and go through all of the machinations of setting it up within LastPass, etc, for something that I might only be logging into two or three times in my entire life, I have a decoy email address, an address that I only use to test drive different tools, and I only use one password with that because I can easily remember it. I know it's not the most secure thing in the world, but if I decide that I'm going to actually purchase the service or sign up to use it long term, then I will use a proper, I will go through proper registration and enroll with my proper email address or a proper login ID and a secure password in two-factor authentication if it's available. I only use the decoy address when I'm in the test drive phase for any one application. It's a little bit of a lazy approach, but I think it's eminently practical. So you may consider using decoy email addresses as well. Now let's go back to the Breach Report and fill you in on some of the other services that they offer and tell you a little bit more about the story of the Breach Report. A monitoring service that's gonna monitor the web for your email address. But when you first set up and test out Breach Report, you'll notice right here on their homepage, that they offer you to enter your email address or a domain. And this is a peek at the depth of the services that Breach Report offers. Now we can all see the value in having our own personal email address monitored, and having reports coming back if it happens to be included in a hack or a breach somewhere. So there is a lot of value there. But as much value as we find personally with our email address, there is so much more value to be gleaned by domains in companies having their entire enterprise being monitored for. Think about a small company with 10 or 20 or 100 or 1,000 employees, that's a lot of email addresses out there. That's a lot of exposure and Breach Report being able to return when email addresses occur in different breaches is incredibly valuable information for network administrators and companies to have access to. So how much does Breach Report cost to use? For a personal email account, for a single email address, it's 499 a month or $50 a year. Additional email addresses, say for your family, are added on at $1 and 99 per additional email address. So that's it from a personal perspective. As far as monitoring your business goes, they have plans that start at $10 a month for one domain and about 11 email addresses, all the way up to much larger accounts for larger businesses and for enterprise, you're gonna wanna reach out to them and talk to them because they have software that will actually run right on your own servers that will assist you in the entire process. So they have a wide breadth of different services available to you. There's a lot of bad people out there and they're very smart. It's a shame that they don't use their talents for good. But no, they use their talents to try and steal our information and try and make money the ill-gotten way. Thank goodness there are some good services out there like our password managers and monitoring services like Breach Report that give us some assets to help protect ourselves. But the bottom line is you have to be proactive as well. You have to monitor your own information, you have to install password protection, you have to use the tools, change your passwords, and be diligent. It's your responsibility at the end of the day to keep yourself safe online. As this opened your eyes, if it has, you can do me a few favors. You could share this video with others, give us a thumbs up and comment. I would look forward to all of your comments and suggestions in YouTube comments. I promise you I read each and every one even if I don't have time to reply to them all. Now if you have not yet subscribed to Dotto Tech, what the heck are you waiting for? Click on that subscribe button and ring the notification bell and I will see you next time for more Dotto Tech. Until then, I'm Steve Dotto. Have fun storming the castle.
I’ll be honest: I don’t particularly take joy in talking about topics like this, and I wish that all of my posts could be about lighthearted and entertaining stuff. I mean, the world’s already bleak enough as it is. Sadly, what we’re going to talk about today, account breaches, is a very real problem—one that puts us all in danger 24/7. And you’d know exactly what I’m talking about if you’ve ever asked yourself this simple question: “Have I been hacked?”
Email address security isn’t exactly something that dwells on our minds every day, and with good reason. To be able to access many of the online services we use in our daily lives, we end up having to provide our email addresses and other personal information. We do so with the implied understanding that the websites we sign into will do everything in their power to keep our information safe.
Unfortunately, hackers put in the same amount of effort to get our information—and when they succeed, more often than not, we only find out when it’s already too late.
How hackers attack
Here’s what you should understand about account breaches: they’re not always our fault. In fact, some of the most serious instances of information theft happen beyond our control.
There are two different types of attacks:
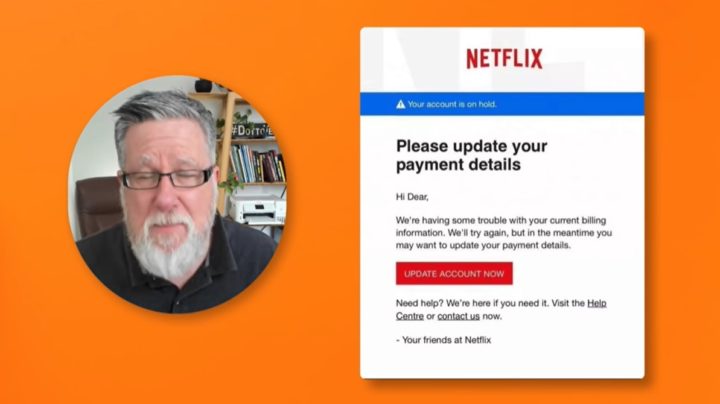
Phishing attacks – Have you ever received an odd-looking email telling you that there’s something wrong with, say, your Netflix account and inviting you to click a button to fix it? That’s one example of a possible phishing attack. In these cases, hackers come after us individually, attempting to steal our information from right under our noses. Fortunately, these types of attacks are easy enough to deflect: Just don’t click on any suspicious links, period. In this case, knowing is indeed half the battle; the other half is self-control.

External attacks – Now, these are the types of attacks that turn out to be massive security headaches. Instead of targeting individuals, external attackers hit websites that provide services people sign up for. Once a website gets breached, the hacker may find themself able to access a treasure trove of user information. If the website owners know a thing or two about account security, then odds are that the hacker will end up with encrypted data that they can’t read. Often, though, the hacker manages to get plain text information: from email addresses to credit card numbers to addresses. In other words, personal information that no self-respecting user would share with anyone else willy-nilly.
What’s in it for the hacker?
Unsurprisingly, 99.9% of the time, it’s for profit.
When hackers get access to our personal data, there are a myriad of ways they can make money off of it.
Some hackers will hold your information hostage, asking you for sums of money to keep them from giving your data to other, more unscrupulous individuals.
Others will just straight-up sell your data on the Dark Web.
But that’s not the scariest part of all this, oh no.
Fact is, It takes an average of 209 days – yes, that’s almost 7 months – from the time a breach occurs to the time the public’s informed about it, regardless of whether or not the website owners find out about the breach a bit earlier.
Worse, it takes roughly 314 days—10 and a half months!—for these websites to fix a breach.
In other words, many of the breaches we hear about now… actually happened last year.
Now that we know the kind of danger we’re in on a daily basis, the question is: what can we do about it?
Has Your Account Been Breached? Email Address Security Tips

First, there’s perhaps no such thing as a website that has never experienced these kinds of attacks. In fact, some websites are under siege pretty much all the time, whether from hackers or the bots they use to steal information. There are probably thousands of website breaches that we’ll never even find out about, even if you’re one of those sites’ account holders.
Luckily, there are some proactive practices we can adopt.

Have a good password strategy in place.
The first step here is to have a password manager that takes care of all your passwords. It doesn’t matter which password manager you use, because all of them will definitely offer you more protection than you’d have if you relied on typing your password manually.
Aside from that, make sure to change your password on a regular basis. The frequency of these hacks should make it clear that this is something you have to do. A good password manager can help you with that, as it will remind you when it’s time to change your password.

Use two-factor authentication.
Here’s another tried and tested strategy that a lot of people seem to disregard. Most major websites support two-factor authentication, simply because it’s so effective. Even if your email address and password get compromised, the additional step will protect your account and information from prying eyes.
Use a decoy email address for sites you’re not 100% committed to.
We’ve all gone through this experience: We visit a site or service that we want to take for a test run, but we’re not sure if we want to use it regularly. Maybe we’ll log into that site twice or thrice for the rest of our lifetimes. In those cases, instead of using my email address and going through the machinations of setting it up, I just use my decoy email address. That way, even if it falls into the wrong hands, I won’t lose much.
Check Your Email Address Security With Breach Report
Meanwhile, services such as Breach Report keep us informed when our email addresses and accounts have been compromised.
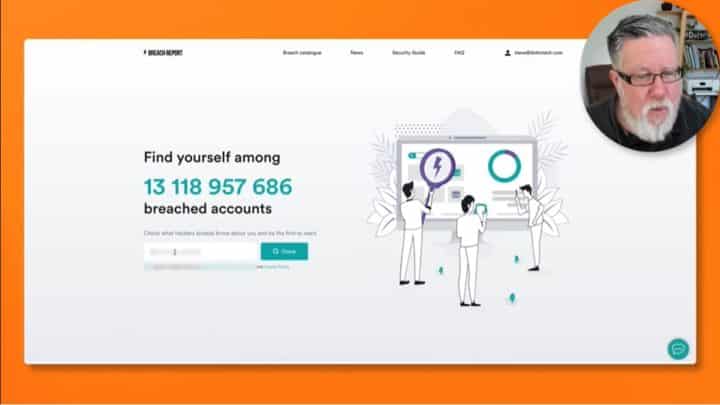
Breach Report is constantly monitoring the web and the Dark Web to find information about breaches. If the site discovers that our information has been included in one of the breaches or leaks, it will inform us right away.
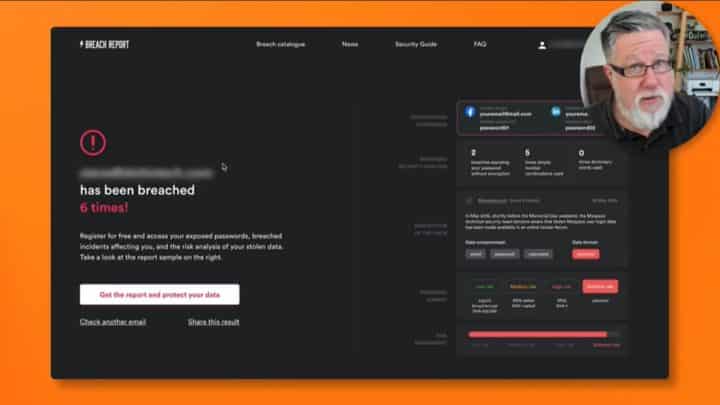
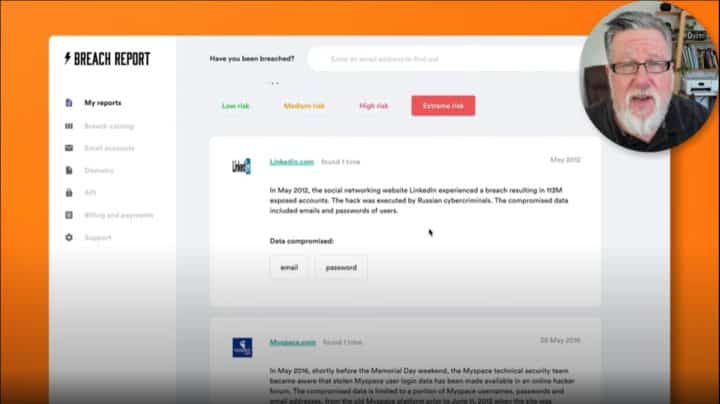
The standard report the site generates takes you through each of the breaches your email address has been discovered in. With that information, you can take action.
What I love about Breach Report, though, is the Breach Catalog, a compilation of known breaches that’s updated as new breaches are detected.
Try it yourself by going to the Breach Report and entering your email address or domain name. Breach Report will do a quick scan, and you’ll know how often your email address has been compromised in no time.
Ultimately, though, Breach Report and other services can only do so much. At the end of the day, it’s your responsibility to keep yourself safe online.
Important links:
- Check if your email has been breached here on Breach Report
- Password Managers
- 2 Factor Authentication – What is 2FA?
- Sync – Is it Time to Drop Dropbox?
- LastPass Family: What you need to know
- Have You Been Hacked?
- DuckDuckGo vs Google: Is DuckDuckGo Better for Your Online Privacy?
- What does Google know about me? How to protect your privacy in 2018
- Protect Your Facebook Privacy With These Simple Tips
Do you need to
STEP up your productivity?
If your answer is YES, then you should sign up to our free weekly Webinar Wednesdays to go behind the scenes and get tips and tricks on how you can 10X your productivity and become a better content creator.



